As residents in the Information Age, we consider ourselves clever sorts. We no longer waste hours on bar stools arguing about the year of Joe DiMaggio’s 56 game hitting streak. Before someone rebuts with his second “nuh-uh” we’ve smart-phoned the answer: 1941
But are we right?
I just got the answer by Googling. Like most people, I clicked the first link of the search results. In many cases, that link goes to Wikipedia and this was no exception. The free encylopedia is an excellent source of information but like all sources, it’s prone to error. So unless our bar bet is substantial, we probably won’t cross reference the findings. “I guess the next round is on me…”
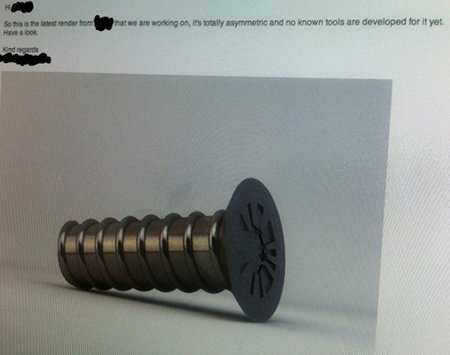
Was this new Apple new proprietary locking screw designed to keep customers from opening their phones? (© 2012 Imgur, LLC)
That was certainly the case when a Swedish firm broke the news about Apple’s new iPhone screws. They were designed specifically to prevent its owner from opening the phone. Given Apple’s penchant for limiting access to the owners of its products, the story struck a nerve. It was picked up by MacWorld, Wired and Yahoo and spread across the Internets.
There was just one problem: the story wasn’t true. Oh, it was truthy. It struck most readers as the type of thing Apple would do but it was a hoax all the same.
The locking screws were fabricated by a Swedish company named Day4. Their intent was to see how easiliy they could spread disinformation. They designed a peculiar screw and posted it to Reddit along with the following message: “A friend took a photo a while ago at that fruit company, they are obviously even creating their own screws.”
That’s it. Neither Apple nor its phone were mentioned in the message. But Day4’s timing was excellent. iPhone 5 is expected to be announced in September and tech media outlets are jonsing for information. If those outlets would have cross-referenced their information, they would have discovered it was all from a single source. That should have raised red flags. Would those flags have halted publication? I don’t know. Everyone wants to be first with a scoop.
In the Information Age, it is often consumers – not distributors – who must perform integrity checks. When a politician stone-cold misrepresents information, the media rarely corrects his inaccuracies. Instead it notes that the other side disagrees. Instead of a debate in which we’ve established the facts, we tend to argue with two separate sets of “facts.”
On this site, I’m not driven to publish scoops. The Day4 prank is already several days old. All the code and configurations you’ll find here were tested before publication. My facts are generally double-checked. And with regard to the event that accompanies this story, you can confidently assert that Joe DiMaggio batted safely in 56 straight games back in 1941. That information is confirmed by multiple sources….


