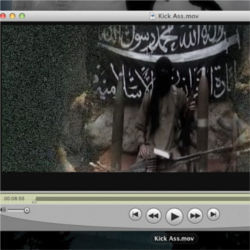
 In 2011, an al Qaeda operative named Maksud Lodin was arrested in Berlin. Among his possessions was a memory card that contained, among other things, a porn video called KickAss. While that may have raised eyebrows — “a religious holy warrior is carrying beat-off material?” — it wasn’t what authorities were after. To them the “good stuff” is actionable intelligence. According to die Zeit, they found it. Federal police recovered al Qaeda documents that were hidden on the card. Where? The were embedded in the film.
In 2011, an al Qaeda operative named Maksud Lodin was arrested in Berlin. Among his possessions was a memory card that contained, among other things, a porn video called KickAss. While that may have raised eyebrows — “a religious holy warrior is carrying beat-off material?” — it wasn’t what authorities were after. To them the “good stuff” is actionable intelligence. According to die Zeit, they found it. Federal police recovered al Qaeda documents that were hidden on the card. Where? The were embedded in the film.
In total, the Germans recovered 141 separate text documents hidden within a .mov file. The discovery confirmed a long-standing hunch that al Qaeda used steganography to hide its information in plain sight. The public was outraged and horrified. “OMG! Al Qaeda is embedding shit inside our porn!!11!1!!”
Your JoeDog was reminded of al Qaeda’s porn when he stumbled across timeshifter. It’s a small utility that lets you to embed messages in regular network traffic. How does it work? By modifying the time intervals between packets, @anfractuosus is able to hide messages in plain site. The system relies on binary encoding. A short delay means 0 and a long delay means 1. By sending messages in this manner, the transmission is unlikely to arouse suspicion.
To implement this system, you’ll need the libnetfilter_queue library and the ability to set iptables rules. All the code is available along with detailed instructions. Check it out.
[anfractuosity: Timeshifter]


